Security for mobile devices on the go
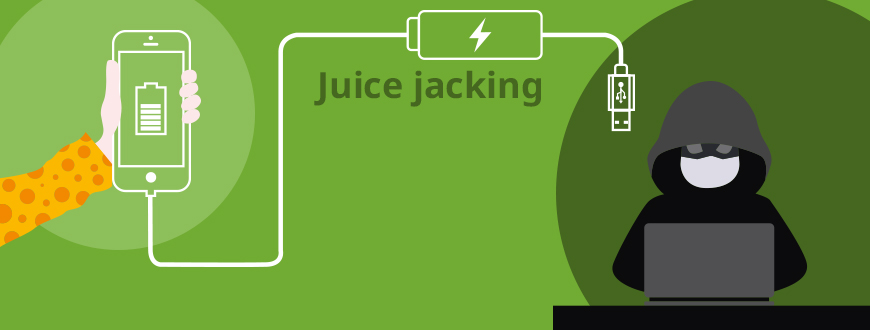
Hack via USB / Juice jacking and how you can prevent it
The USB connector, Universal Serial Bus, is designed to transfer current on the one and data on the other hand. Exactly for that reason, it is universally usable, which is its great advantage. In this article, however, we will show you the disadvantage of this universality, and how to face the danger of data theft and the infection of mobile devices via USB.

(Photo by Daria Nepriakhina on Unsplash)
Which danger does the name juice jacking mean?
Well-known is the danger of catching malware, for example, a Trojan, via an infected USB stick. However, what many users are not aware of at first is that the charging cables of mobile devices also pose a risk. The criminal phenomenon is called juice jacking.
This name came up, for the first time officially, in the year 2011 in the USA. The particularly in the United States known specialist for internet and computer Security, Brian Krebs, coined the term when he reported about it for the first time (see below for a little historical excursus if interested in.)
Juice is current, and jacking refers to hijacking and the robbery of people or the theft of things. So firstly, juice jacking means the hijacking of data and is secondly used to name the compromising other people's equipment to harm the devices and their users.
The basis is that an unlocked mobile phone can be almost completely read out, depending on the security settings. However, since many users are not aware of this danger and thus do not pay attention to it in their security settings, they open up the danger of hacking their hardware as soon as they enter an "unprotected" connection between their mobile device and foreign connectors.
What is juice jacking in detail?
In simple words, juice jacking uses a security gap. It is the most innovative and contemporary method to hack mobile devices. This security gap arises as soon as a mobile device e.g. a smartphone is supplied with current via the USB port while plugged into or connected to another (foreign) device. Examples for foreign devices are charging stations or points in publicly accessible places, for examples in cafés, trade fair or exhibition halls, shopping malls, hotels, air ports or railway stations.
Comparable to manipulated ATMs that have an attachment to save pin codes, charging stations can be manipulated, too. That is called a compromised USB charging point. The computer inside the charging station can be infected with malicious programs, either to pull (= copy) data from the device or also to smuggle malware onto the connected device. Depending on the amount of data and the duration of the unprotected connection, the contents of the entire mobile device can be copied and passed into unauthorized hands.
Malicious or malware infections can, for example, consist of malicious code, Trojans, spyware, or keyloggers, which can, among other things, also enable complete control over the attacked system. Another form of USB port hacking is where the malicious code installed on the victim's single device is programmed to damage all future USB charging points/ports it comes into contact with. This allows the hacker to penetrate multiple systems.

(Photo by Jakob Owens on Unsplash)
The robbery of data is the actual juice jacking. Both kinds of criminal operations - firstly, the infection with malware and secondly, the copying of foreign data - are mostly not or too late recognized, so further criminal actions (for example extortion of the victim, online purchases in its name and at its expense, etc.) are enabled.
Technical background: For what reason works this kind of hacking?
The USB port enables the transmission of electricity, so current, and also data. By this property, it is an extremely universal connector. The smartphone is, in a wider meaning, data storage with many practical functions. The power supply is via USB, and by USB, the smartphone can receive and transfer data.
The sticking point is that charging and data streams cannot be strictly separated. As soon as a smartphone or other mobile device is connected to a power source (PC, charging station, etc.) via USB, data can also be transferred at the same time, in both directions. The simultaneous data transfer even enables higher currents than 100 mA, so it can be charged faster than if only voltage is provided. There is a risk of hacking as soon as a mobile device is connected to a PC, a notebook, or a public charging station via the USB port for charging.
What can offer protection - how can you safely charge your mobile device on the move?
Completely safe is to connect and load the mobile device via the original, supplied power supply unit, as long as the power adapter is directly connected to a pure electricity source. But attention: As soon as, for example, the power supply unit is disconnected from the USB cable and the cable USB to USB plug, or Lightning to USB plug, is connected to a foreign USB female port, the risk is there again.
Secondly, pure charging cables can be used, which do not allow data transfer because they do not have any lines for this purpose (e.g. from Delock, see below). Power banks are just as useful. These can be safely charged on other people's PCs or power supplies. To charge your mobile device via your power bank, there is no longer a connection to the external PC or power supply unit.

(Photo by Austin Distel on Unsplash )
Equally secure protection is provided by a data blocker, also known as a "USB condom". This special kind of adapter has a USB female on one and a plug on the other side. If the adapter is attached between the (foreign) charging cable and the own smartphone, that means switched in between, then the data transfer is blocked. Now only current is led into the mobile device, as only the contacts for the power supply are connected, but not the data lines.
Small excursus: Points on the history and relevance of juicejacking
As mentioned above, the term was coined by Brian Krebs in 2011. Krebs is still active as an internet and computer security consultant. He had already begun intensive work on the topic in 2001 when his home network had become the successful target of a hacker attack.
Krebs explained that it is quite possible for attackers to set up a fake public charging station and hide a small computer inside. If a smartphone or tablet is then connected with a normal USB cable, the hidden computer can inject malicious code or steal sensitive information such as the contact list, emails, or other data stored on the device.
During the hacker event DEFCON 2011, stations for "free charging" were set up by the company Wall of Sheep. When using them, the visitor saw the message: "You should not trust public charging stations with their devices". The aim was to make visitors aware of the danger. In 2012, security researcher Kyle Osborn published a programming framework for connecting an attacking device to a victim device. In this way, the attacked device could be unlocked to gain access to data and carry out further manipulations.
In the period that followed there were developed additional malware for research purposes, for Android as well as iOS. Apple and Android developers responded by developing security measures to minimize the attack points. But still, the security gap "USB Port" could not be closed completely!
Here in Germany, there are maybe not so many public charging stations. But when traveling for business or vacation purposes, and often also in cafés, railway stations, or public transport, most probably you will be confronted sooner or later with the situation: The mobile device needs juice, but your charging cable and power supply unit are not at your hand, or you cannot use it, for example, because no pure current source is available.
Product examples by Delock
All items shown here enable secure charging.

Item 65965
Adapter EASY-USB Type-A - Data blocker
- 1 x EASY-USB 2.0 Type-A male to 1 x USB 2.0 Type-A female
- USB-A male port usable in both directions
- Output current: up to 500 mA
- Dimensions (LxWxH): ca. 37 x 18 x 11 mm

Item 87866
USB Charging Cable für iPhone™, iPad™, iPod™
- 1 x USB 2.0 Type-A male to 1 x 8 pin Apple Lightning™ male
- Cable gauge: 24 AWG
- Output current: up to 3 A
- Length incl. connectors: ca. 30 cm

Item 87884
USB Type-A + USB-C™ Charging Cable 4 in 1
- 1 x USB 2.0 Type-A male + USB-C™ male to 2 x 8 pin Apple Lightning™ male, 1 x USB Type Micro-B male, 1 x USB-C™ male
- Cable with textile shielding
- Length incl. connectors: ca. 1.20 m

Item 86820
USB-C™ Charging Cable 3 in 1
- 1 x USB 2.0 USB-C™ male to 1 x 8 pin Apple Lightning™ male, 1 x USB Type Micro-B male, 1 x USB-C™ male
- Cable with textile shielding
- Length incl. connectors: ca. 30 cm

Item 85850
USB Type-A 3 in 1 Retractable Charging Cable
- 1 x USB 2.0 Type-A male to 1 x 8 pin Apple Lightning™ male, 1 x USB Type Micro-B male, 1 x USB-C™ male
- Flat cable
- Length incl. connectors & housing: ca. 98 cm

Item 66497
Adapter USB 3.0 Type-A - Data blocker
- 1 x USB 3.0 Type-A male to 1 x USB 3.0 Type-A female
- Output current: up to 900 mA
- Gold-plated contacts
- Dimensions (LxWxH): ca. 45 x 17 x 11 mm

Item 66528
Adapter USB-C™ to Type-A - Data blocker
- 1 x USB-C™ male to 1 x USB Type-A female
- Output current: up to 2.4 A
- Dimensions (LxWxH): ca. 35 x 19 x 10 mm

Item 85356
USB-C™ Charging Cable PD 5 A with E-Marker
- 1 x USB-C™ male zu 1 x USB-C™ male
- Output current: up to 5 A
- Length incl. connectors: ca. 15 cm